See the forest for the trees: glimpse the storyline of an attack using MITRE tags
With compute infrastructures being monitored quite closely these days, many events and alerts are created and collected at all times. While individual events and alerts are of course important, it is often hard to understand a more complex attack operation in the sense of seeing the bigger picture from the detailed events. We lately have experimented to see how one could possibly find the storyline of an attack operation by abstracting from the details with the help of MITRE tags. The MITRE ATT&CK® framework defines a “globally-accessible knowledge base of adversary tactics and techniques based on real-world observations”, i.e., describes the different kinds of possible attack steps in a systematic way. For each of the documented techniques/sub-techniques the MITRE ATT&CK includes textual context, examples, ways of mitigations and detections and references. These techniques are in turn structured into a set of 14 high-level tactics, like reconnaissance, initial access, privileged escalation etc - and we try to use these MITRE tactics as the high-level abstraction in our experiment. Very interesting is in this context that MITRE tags are independent from any particular tool, it is therefore easy to fuse alerts generated by different monitoring tools on that level.
For testing we have set up a small environment with Linux and Windows VMs together with monitoring components (SysFlow, Symon/Sigma rules/ElastAlert, Snort). While using the intentionally vulnerable OWASP Juice Shop as the main attack surface, we created a multi-stage attack scenario involving reconnaissance operations, attacking the web shop, defacement, data exfiltration, lateral movement and backdoor installation - and collect the alerts from the monitoring components while running this scripted attack. The collected alerts are mapped via their MITRE tags to a time-series of high-level MITRE tactics with the goal to see whether this approach can be helpful to gain an overview and higher-level understanding of the storyline and attack goals.
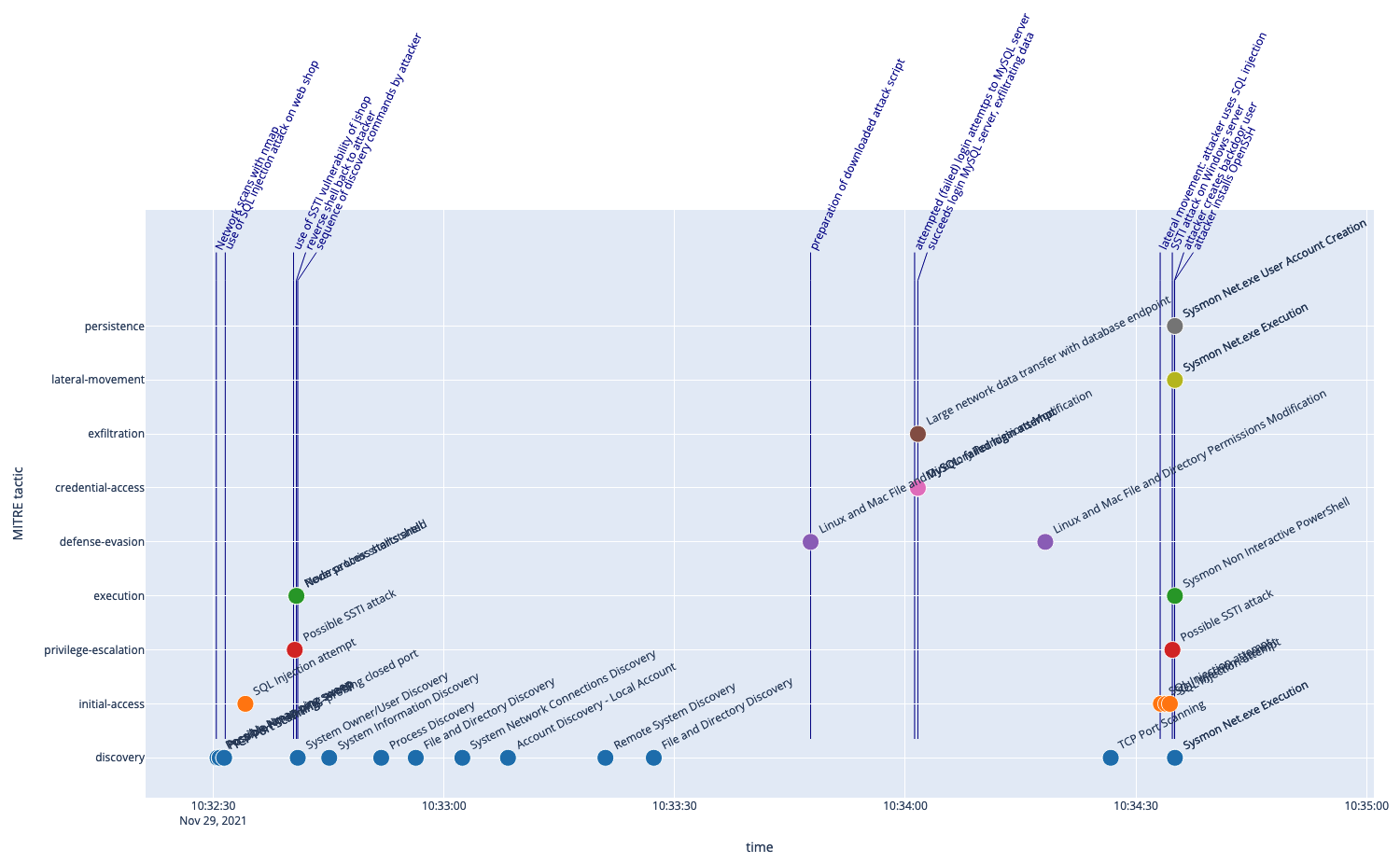
The following figure shows the timeline for the attack with marker symbols representing the collected alerts and the MITRE tactic derived from the tags (vertical axis), together with annotations from the log of our scripted attack as our ground truth to compare (annotated vertical lines).
The marker symbols tell a story of an attack starting with discovery steps, progressing to access and execution, with a potential privilege escalation. We also find in the later phase some failed attempts to log into a database followed by a large data transfer - indicating a potential successful break-in with data exfiltration. Another round of discovery operations precedes more alerts with a similar sequence of access-escalation-execution and alerts tagged as lateral movement and persistence.
Comparing this with the ground truth data from our knowledge of the scripted attack shows that many steps as well as the overall progression of the attack are nicely reflected in the alerts and the associated MITRE tactics. Of course not all steps of the attack leave traces in the alerts, nor do we understand from this view alone what is going on in detail, but we could imagine this as a complementary view ideally making the larger context visible beyond the details of all alerts, triggering follow-up investigations (e.g., here what the attacker was later doing with the user account he was able to create).
Please have a look at the details of this approach in the Jupyter notebook - which you also can take as starting point for your own experiments.
This is work-in-progress - more work will be required to evaluate this approach with more attacks in more complex environments, but have a look and let us know if you find this promising and interesting to pursue!